Overview
This article explains how to troubleshoot a specific subscriber in roaming when messages fail due to an anti-spoofing rule.
Troubleshooting
The first thing to investigate is the Syslog, filtering messages related to the A-party number. In the example below, the A-party is 999999999, and the following messages can be observed, indicating that MO messages from A-party were considered spoofed, thus getting blocked by the system.
textpass@customer-rtr log]$ grep 999999999 messages
Oct 17 00:54:46 customer-rtr snmptrapd[3533]: 00:54:46 TRAP6.TEXTPASS-SMS-MIB::fwMoFwdSmWithSpoofedOriginatorAddress TEXTPASS-SMS-MIB::fwTrapOriginatorAddressInMoFwdSm.0 = STRING: "51999999999" TEXTPASS-SMS-MIB::fwTrapMscOrSgsnAddressInMoFwdSm.0 = STRING: "5288888888888" TEXTPASS-SMS-MIB::fwTrapMscOrSgsnAddressInSriSm.0 = "" TEXTPASS-SMS-MIB::fwTrapImsiInMoFwdSm.0 = "" TEXTPASS-SMS-MIB::fwTrapImsiInSriSm.0 = "" TEXTPASS-GEN-MIB::deviceType.0 = STRING: "RTR" from customer-rtr
Oct 17 01:07:49 customer-rtr snmptrapd[3533]: 01:07:49 TRAP6.TEXTPASS-SMS-MIB::fwMoFwdSmWithSpoofedOriginatorAddress TEXTPASS-SMS-MIB::fwTrapOriginatorAddressInMoFwdSm.0 = STRING: "51999999999" TEXTPASS-SMS-MIB::fwTrapMscOrSgsnAddressInMoFwdSm.0 = STRING: "5277777777777" TEXTPASS-SMS-MIB::fwTrapMscOrSgsnAddressInSriSm.0 = "" TEXTPASS-SMS-MIB::fwTrapImsiInMoFwdSm.0 = "" TEXTPASS-SMS-MIB::fwTrapImsiInSriSm.0 = "" TEXTPASS-GEN-MIB::deviceType.0 = STRING: "RTR" from customer-rtr
Oct 18 10:22:55 customer-rtr snmptrapd[3533]: 10:22:55 TRAP6.TEXTPASS-SMS-MIB::fwMoFwdSmWithSpoofedOriginatorAddress TEXTPASS-SMS-MIB::fwTrapOriginatorAddressInMoFwdSm.0 = STRING: "51999999999" TEXTPASS-SMS-MIB::fwTrapMscOrSgsnAddressInMoFwdSm.0 = STRING: "5266666666666" TEXTPASS-SMS-MIB::fwTrapMscOrSgsnAddressInSriSm.0 = "" TEXTPASS-SMS-MIB::fwTrapImsiInMoFwdSm.0 = "" TEXTPASS-SMS-MIB::fwTrapImsiInSriSm.0 = "" TEXTPASS-GEN-MIB::deviceType.0 = STRING: "RTR" from customer-rtr
The errors above indicate the MO Anti-Spoofing check failed for A-party 51999999999 because there was no response for the SRI-SM sent from Lithium SMSC to the HLR, or the SRI-SM response was returning some error.
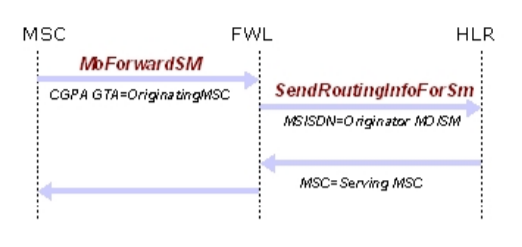
The diagram below illustrates the call flow for a MO/SM being checked for spoofing.
Since Lithium SMSC could not validate the MSC/VLR information for this originator, the firewall was blocking it as a MO-spoofed message because of the following setting:
[textpass@customer-rtr log]$ tp_walk fwProperties | grep -i MoAction
fwPropMoActionForOriginatingAddressSpoofing.0 = INTEGER: discardWithNak(4)
You can verify if the responses are not reaching the SMSC by checking if the SRI-SM timeout counter increases:
$ tp_walk smsCntSriSmTimeoutCounter
smsCntSriSmTimeoutCounter.0 = Counter32: 29
And after a while:
$ tp_walk smsCntSriSmTimeoutCounter
smsCntSriSmTimeoutCounter.0 = Counter32: 51
Solution
To bypass the MO Anti-Spoofing, you need to check and allow the message to be sent. You can include the originating MSC/VLR GT to the whitelist of MSC Global Titles (GTs) that the FWL will consider trusted.
-
Check the Syslog on Traffic Elements indicating MO-spoofed messages that should be allowed (i.e., for the specific subscriber complaining).
[textpass@customer-rtr log]$ grep 999999999 /var/log/messages*
Oct 17 00:54:46 customer-rtr snmptrapd[3533]: 00:54:46 TRAP6.TEXTPASS-SMS-
MIB::fwMoFwdSmWithSpoofedOriginatorAddress TEXTPASS-SMS-
MIB::fwTrapOriginatorAddressInMoFwdSm.0 = STRING: "51999999999" TEXTPASS-SMS-
MIB::fwTrapMscOrSgsnAddressInMoFwdSm.0 = STRING: "5288888888888" TEXTPASS-
SMS-MIB::fwTrapMscOrSgsnAddressInSriSm.0 = "" TEXTPASS-SMS-=
MIB::fwTrapImsiInMoFwdSm.0 = "" TEXTPASS-SMS-MIB::fwTrapImsiInSriSm.0 = ""
TEXTPASS-GEN-MIB::deviceType.0 = STRING: "RTR" from customer-rtr -
Identify the originating MSC/VLR on the output above, displayed in the following field:
fwTrapMscOrSgsnAddressInMoFwdSm
-
In the
/usr/TextPass/etc/common_config.txtfile, identify the list name assigned to the following parameter:whitelistofmomscforspoofchecksuppression
-
Edit the GT list in the MGR GUI under Routing > Others > Lists. Open the list with the name identified on step 3 and insert the GT address determined in step 2.
-
You can add a GT prefix if needed (for example, 528888*).
-
Save the list.
Disabling the MO Anti-Spoofing Functionality
Consider the procedure below to disable the functionality:
-
Login as TextPass to the MGR node and edit the
/usr/TextPass/etc/common_config.txtfile by changing thefirewallmospoofingcheckconditionfield fromalwaystonever. -
Go to each RTR, restart the TextPass process one at a time. Wait until the process is operational again before proceeding with the next one.
tp_config --validateonly
tp_stop --textpass; tp_start --textpass
tp_status
For more details, please check the NMM Firewall Guide available in the NewNet Download Center.
Priyanka Bhotika
Comments